Zeitpunkt Nutzer Delta Tröts TNR Titel Version maxTL Do 02.05.2024 00:00:10 7.198 +1 575.644 80,0 NerdCulture 4.2.8 500 Mi 01.05.2024 00:00:24 7.197 0 575.080 79,9 NerdCulture 4.2.8 500 Di 30.04.2024 00:00:14 7.197 0 574.573 79,8 NerdCulture 4.2.8 500 Mo 29.04.2024 00:00:13 7.197 +1 574.064 79,8 NerdCulture 4.2.8 500 So 28.04.2024 00:00:18 7.196 +1 573.535 79,7 NerdCulture 4.2.8 500 Sa 27.04.2024 00:00:11 7.195 -1 573.157 79,7 NerdCulture 4.2.8 500 Fr 26.04.2024 00:00:11 7.196 0 572.732 79,6 NerdCulture 4.2.8 500 Do 25.04.2024 00:01:11 7.196 +1 572.250 79,5 NerdCulture 4.2.8 500 Mi 24.04.2024 00:00:12 7.195 0 571.738 79,5 NerdCulture 4.2.8 500 Di 23.04.2024 00:01:14 7.195 0 571.375 79,4 NerdCulture 4.2.8 500
Olly 👾 (@Olly42) · 01/2024 · Tröts: 166 · Folger: 17
Do 02.05.2024 16:51
Dangerous new Wpeeper Android Malware adds a Backdoor to your Phone to steal your Data.
The Wpeeper malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2) servers for detection evasion. Wpeeper has been spotted in at least two unofficial app stores (Uptodown App Store).
http://blog.xlab.qianxin.com/playing-possum-whats-the-wpeeper-backdoor-up-to/
#android #os #wordpress #malware #wpeeper #it #security #engineer #tech #news

Wpeeper relies on a multi-tier C2 architecture that uses infected WordPress sites as an intermediary to obscure its true C2 servers. As many as 45 C2 servers have been identified as part of the infrastructure, nine of which are hard-coded into the samples and are used to update the C2 list on the fly.
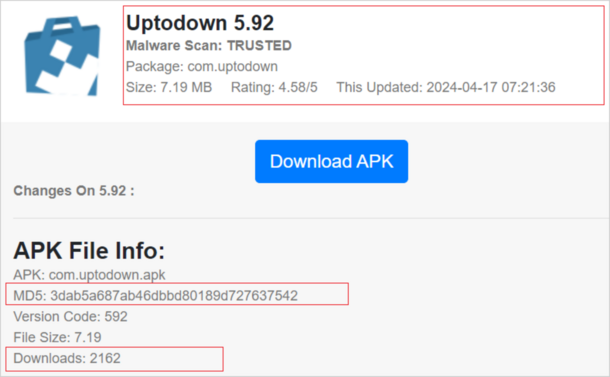
The malicious APK on a third-party app store. The use of the Uptodown App Store app for the campaign indicates an attempt to pass off a legitimate third-party app marketplace and trick unsuspecting users into installing it.
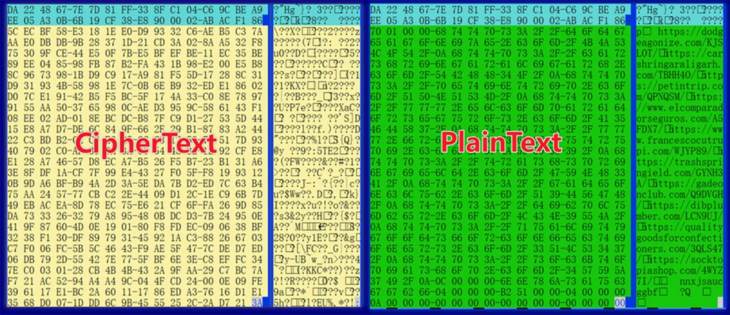
Hardcoded C2 addresses. Wpeeper can update its C2 servers dynamically through the reception of a related command, so if a WordPress site is cleaned, new relaying points on different sites can be sent out to the botnet.
[Öffentlich] Antw.: 0 Wtrl.: 1 Fav.: 0 · via Metatext